
How to configure an IPSec VPN between a Sophos Firewall and a Mikrotik Router where the Mikrotik Router has a dynamic IP.

Overview
The article shows how to configure IPSec VPN Site-to-Site between Sophos firewall and Mikrotik Router where the Mikrotik Router doesn’t have a static public IP address but has a PPPoE connection.
IP Details:
Sophos ( KTM_FW):
- Port B (WAN) : 10.11.12.2/24
- Port A (LAN) : 172.16.16.16/24
Mikrotik (PKR_RTR):
- eth1(WAN): PPPoE Connection (username: branch-user, password: user@12345)
- eth2(LAN): 192.168.2.0/24
Step 1: Configure VPN on Sophos Firewall (KTM_FW)
configuration for ip address has been already configured as diagram.

So, now first we will configure ip host for local and remote Lan networks.


Now, create vpn create profile to match parameters as mikrotik.
Go to Configure > VPN > ipsec policies and click on Add button. Enter the parameter as follows.

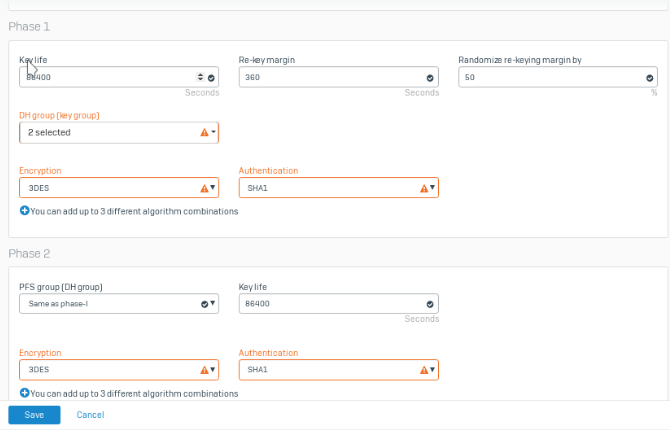
Click on Save.
Now we will create IPsec Connection.
Go to Configure > VPN > IPsec Connections and click on Add button.
Select Gateway type as Respond only and select Policy as we have created. Select Authentication type as Preshared key and enter key.

Here, we don’t know the remote public ip address because of dynamic ip address so we will let it * on Gateway address.

Click on Save button. When clicking Save, the following screen will be displayed.
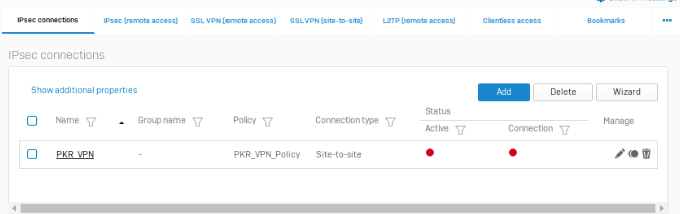
After creating an IPSec connection we need to click on the circle icon in the Active column to turn on this connection.

Now, we will allow vpn traffic from the firewall rule.
Go to Protect > Rules and policies > Add Firewall rule > New firewall rule.

Step 2: Configure VPN on Mikrotik Router (PKR_RTR)
First we will configure PPPoE connection on port eth1 on mikrotik router.
Go to PPP > Interface > + PPPoE Client

Click on Dial Out menu.

Click apply ok. And check the ip address on IP > Addresses.

Now configure LAN ip address on eth2.

Configure NAT to allow internet on LAN networks.

Now we will configure IPSec VPN on mikrotik router.
Go to IP > IPsec
Click on Profiles Tab and click on Plus(+) sign. and enter following parameters

Click on Peers Tab and click on Plus(+) sign. and enter following parameters

Click on Identities Tab and click on Plus(+) sign. and enter following parameters. Enter Secret as same key which we have entered on sophos firewall.
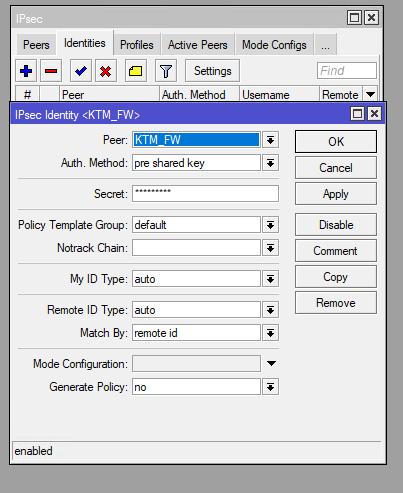
Click on Proposals Tab and click on Plus(+) sign. and enter following parameters.

Click on Policies Tab and click on Plus(+) sign. and enter following parameters

Click on Action Tab.

Click Apply and Ok.
On Mikrotik, we have successfully configured VPN. So now we will allow VPN traffic from firewall rules.
Go to IP > Firewall > Filter Rules and click Add.
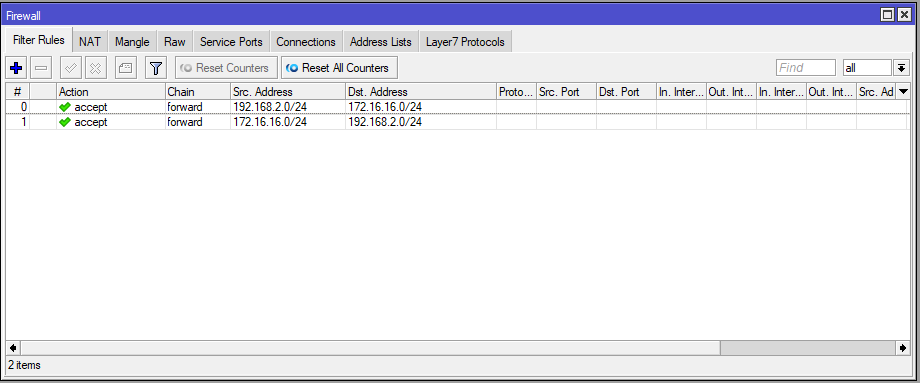
Verification:
Check VPN Status on Sophos firewall.

Check VPN Status on Mikrotik Router.

Pinging Lan network of the Head Office (KTM) from the Lan network of the Branch Office (PKR).

Similarly, Pinging the Lan network of the Branch Office (PKR) from the Lan network of the Head Office (KTM).

If you can’t ping from Sophos XG end you might have to look into this article. Have to add the routes manually so the traffic is passed through the IPSec tunnel.
Issue
When multiple routes for the same destination network exist the route_precedence setting can be used to control the order of precedence between the following types of routes:
- Policy routes
- VPN routes
- Static routes
However, this precedence only applies to traffic where the destination gateway exists in the WAN zone.
If for example, a particular subnet is accessible over an IPSEC VPN and is also covered by a static route directed to a router in the LAN zone, then the route_precedence command cannot be used to control which route is used.
https://support.sophos.com/support/s/article/KB-000038775?language=en_US